The incident which has has been reported today supports our estimation that a targeted attack against a network remains undetected for up to 90-120 days after a successful infiltration. Looking at this figure, ThyssenKrupp's security department was relatively quick in detecting the attack. Past examples show, however, that highly complex espionage programs which have been designed for a specific target or espionage campaign can even, under certain circumstances, remain undetected for up to several years. One such example is the Uroburos framework.
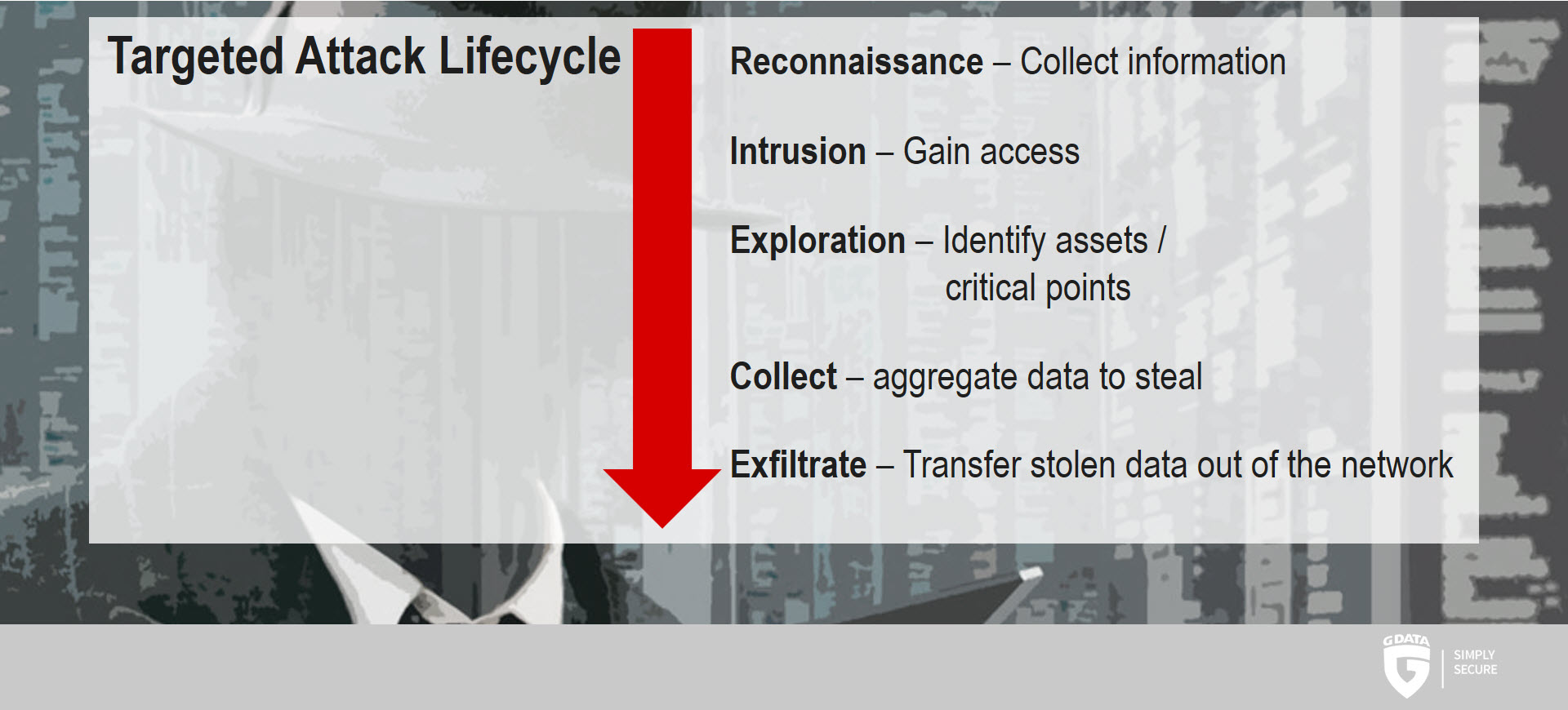
Anatomy of a targeted attack
A targeted attack usually follows a certain pattern. Initially, the attackers gather information about their target. The information which was gleaned during this process is then used to formulate a plan for gathering access. Several ways exist to achieve this, from malicious software to social engineering. Once the attackers have gained access, they try to expand their footprint by securing additional access permissions. Once interesting data has been identified and collected, it is time to exfiltrate and actually steal the data.
There is no definite information on the actual level of sophistication of the tools used in this attack. It should be pointed out, however, that not every espionage tool is custom built for use on only one target. More often than not, attackers use existing tools for their work to keep their own costs low. According to ThyssenKrupp, evidence suggests the attacks may originate from an Asian country.
Large companies are not the only target
Analyses by GE Capital state that last year about 44% of all applied-for patents in Europe are held by medium-sized companies. Therefore it does not come as a surprise that medium-sized companies represent viable targets for criminals. According to the German Federal Office for Information Security (BSI), 58% of all private companies as well as public institutions in Germany have already found themselves subjected to attacks against their IT and communication systems.
Looking Back: Uroburos - highly complex espionage software with Russian roots
In 2014, security experts at G DATA uncovered and analyzed a highly sophisticated and complex piece of malware which was designed to steal data from high-profile networks such as government agencies, intelligence services or large companies. The rootkit named Uroburos worked autonomously and propagated itself throughout a network. It even affected such machines which did not have an internet connection. G DATA concluded back then that a piece of malware with this level of sophistication could only have been realized with substantial funding and investments in skilled personnel. The design and level of complexity supported the conclusion that Uroburos has its roots in the intelligence sector. The analysis further concluded that Uroburos had to have Russian roots. Until it was discovered by G DATA, this highly complex malware had gone largely unnoticed.