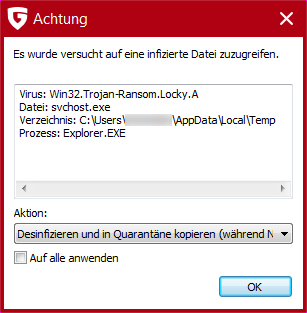
During the last quarter a new trend has emerged. The number of new ransomware families and variants is rising, but most of them seem to be of low quality. Low quality here means they contain flaws, which make decryption without a key possible or have bugs that destroy the files forever. One deciding contributor are the new variants of the Cryptear family. Members of that malware family are based on the open source ransomware Hidden-Tear or its successor EDA2. These source codes had been released on Github by security researcher Utku Sen and were abandoned later. The encryption procedure contains flaws by design to make decryption without a key possible. There are at least 28 documented Cryptear variants today [see also Ransomware Overview], and numerous undocumented Cryptear variants that haven't been noteworthy enough to get media attention. One new Cryptear variant from last week appends the .locklock extension to encrypted files and has adopted the flaws from the original source code [sample’s SHA256: e3d1ea550ecc6c135e729ae2c05ac59ff95991ccbaa3ff90c55b9b7ad258276a].
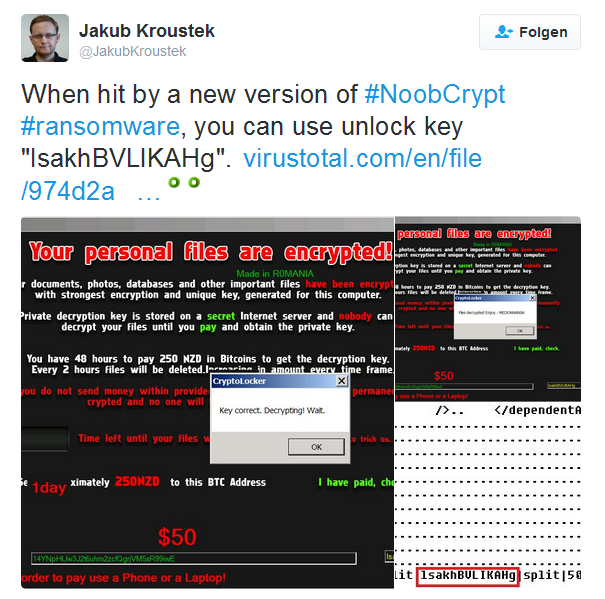
Another open source ransomware by the name my-Little-Ransomware has also been a contributing factor to the release of low-quality ransomware; but there is also a number of new low-quality ransomware families without open source background. Newly discovered families or variants from last week are Stampado, a Xorist variant called XRat, a DetoxCrypto variant called Crypt0, and a ransomware that goes by the name NoobCrypt in the community.
All known variants of NoobCrypt use a hardcoded key for encryption.
Members of the Xorist ransomware family like XRat utilize XOR with a fixed sized key (in contrast to a one-time pad). This kind of encryption is vulnerable to frequency analysis and known-plaintext attacks making it possible to crack the encrypted files.
Stampado's keys can be bruteforced since its first release. The newest variant is no exception and can be decrypted [Sample: 886f7ceded832615e7280445ab0fbbdfcf2493572effb4e36480e81873af180d]. It also targets file extensions that are applied by other ransomware families.

Crypt0 has a bug that may append the file name of the ransom note several times resulting in file names like "HELP_DECRYPT.TXTHELP_DECRYPT.TXT"
Crypt0 can also be decrypted.
It seems that the ransomware business is now reasonable lucrative without putting effort into bug free development or even copying the big players. The big players may have shaped a common mindset in the public that decryption or recovery of ransomware encrypted files is impossible leading enough people to pay ransoms without looking for solutions. Open source projects like Hidden-Tear/EDA2 have made it easy for the less-skilled criminals to create their own flawed ransomware. On the bright side, their intentional flaws and the shameless copying of said flaws opens up ways of recovery, if the victim is aware of the shortcomings.