Busting Myth #1 - "I do not surf on dangerous sites"
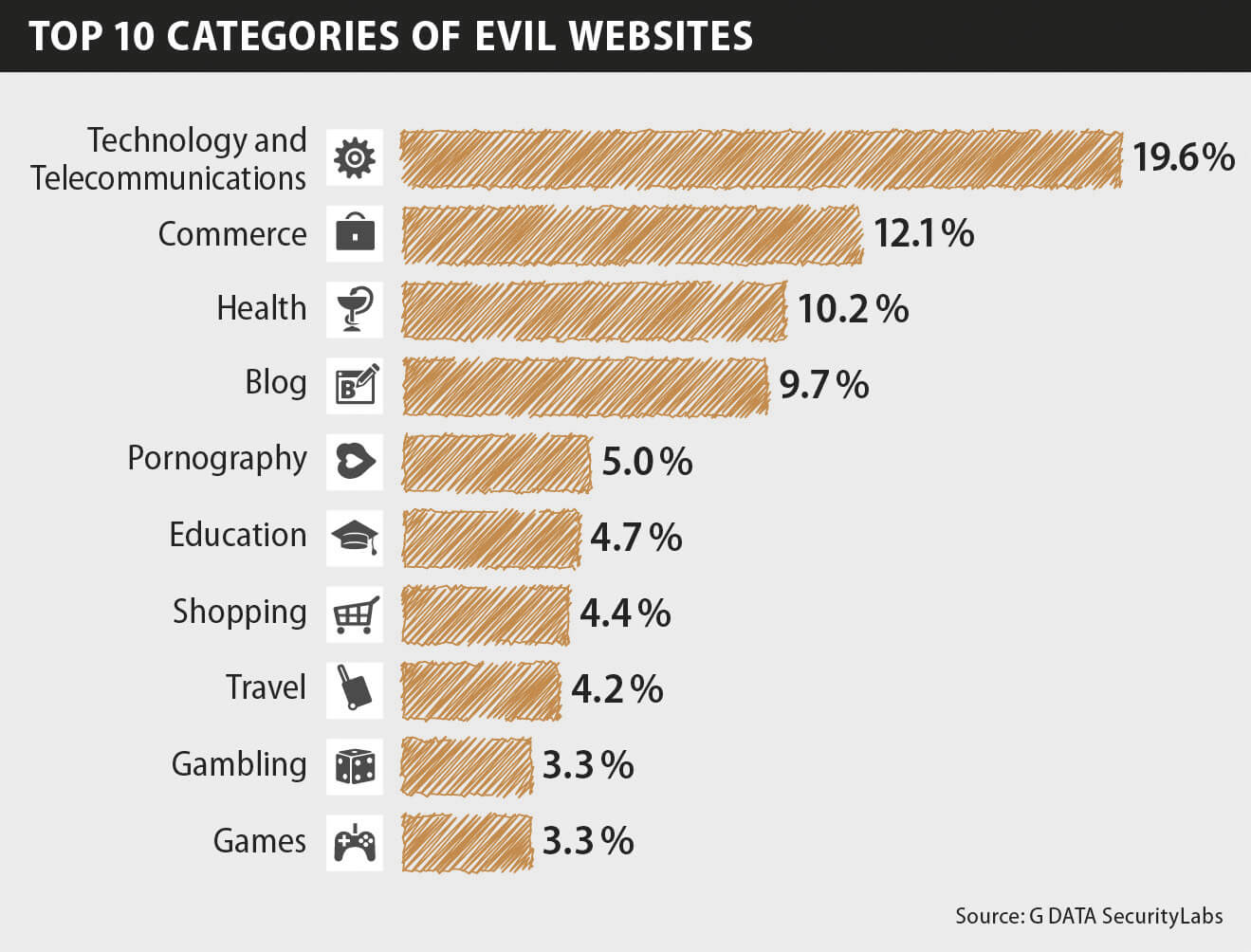
One of the report’s main findings is the fact that evil websites can be found among all topics, not only the ones regarded as nasty. Looking at the second half year of 2014, the top 10 categories accounted for 76.4% of all sites analyzed. It shows that topics which are usually regarded as decent, such as technology, health or travels, are amongst the top ones. In contrast, sites involving pornography or gambling have a lower impact.
Attacks can take place everywhere on the Internet. There are some subject areas that harbor a higher risk of infections, but no subject area in itself is completely evil or harmless. Attackers are focusing on current topics but, other than that, they are relying on untargeted attacks that are quick to execute, for example, through the mass infection of websites with security vulnerabilities. This means high profits with little effort.
Busting Myth #2 - "My computer is not valuable for cyber attackers"
Each and every computer does have a value for attackers, in many different ways.
Infected PCs can be integrated into botnets and misused as e.g. a proxy, used as spam sending bots or as an instrument for DDoS attacks against other systems. In other cases, users’ computers CPU time and energy are used to mine virtual currencies, such as Bitcoins. The report indicates that the amount of new malware types that are used for various attacks against computer users rose significantly during the second half of 2014. The experts registered 4.150.068 new malware types, an increase of 125% compared to the first half year, leading to an overall number of almost six million during the past year. Malware connected to the creation and maintenance of botnets have a serious share in these statistics.
Furthermore, a lot of the data that can be found on computers is a valuable good for the attackers as well: they read email addresses from the address books, they might find unprotected passwords to accounts they can misuse and one should not underestimate personal data stored in photos, documents, etc. These digital items can be sold on underground markets or used to blackmail the affected user.
The Internet can be a dangerous place to surf, but there is no need to be worried. But it is a fact that computers without proper security measures are easy bait for crooks. The price paid while being infected with digital debris is likely to be much higher than the costs for a comprehensive security solution.
Read more interesting facts and statistics in G DATA’s Malware Report H2 2014